Monitor and Automate MTA-STS with Cert Spotter
By default, email is insecure: any email sent to your domains is at risk of being intercepted and read by network attackers. Even if your domains support STARTTLS, an active attacker can downgrade the connection to plaintext. MTA-STS changes that. It's a new standard that lets you publish a policy requiring that inbound email to your domains be encrypted in transit using authenticated STARTTLS. Major providers like Gmail already support MTA-STS. If your domains receive email, whether via a third party provider or your own mail servers, you should consider deploying MTA-STS.
However, MTA-STS is tricky to deploy correctly, and a mistake can prevent email from getting through. MTA-STS imposes specific requirements on your domain's mail servers; if the mail servers fall out of compliance, due to problems such as an expired or incorrectly-installed certificate, you'll lose email. If your MTA-STS policy falls out of sync with your domain's DNS, you'll lose email. The antidotes are monitoring to detect mistakes, and automation to prevent mistakes in the first place. Cert Spotter now does both: monitor your domains for MTA-STS problems, and automate the publication of correct MTA-STS policies.
Monitoring
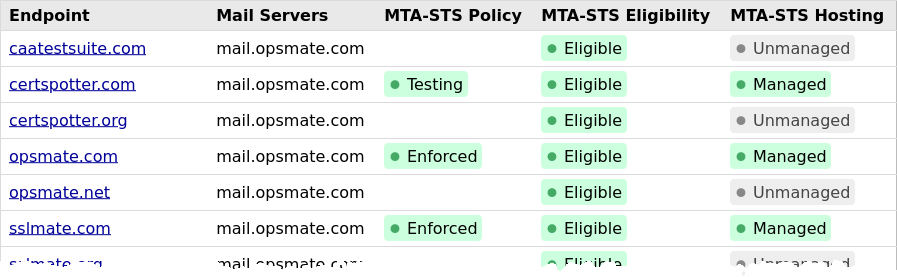
Cert Spotter continuously monitors your domains' MTA-STS policies and alerts you if a problem would prevent the delivery of mail. Cert Spotter automatically detects MTA-STS policies for any of your monitored endpoints; you don't need to enable MTA-STS monitoring separately.
Among the problems detected by Cert Spotter are:
- A mail server is not eligible for MTA-STS (doesn't support STARTTLS with TLSv1.2 or higher, or has an expired, mismatched, untrusted, or otherwise invalid certificate).
- The MTA-STS policy can't be retrieved or is invalid.
- The MX servers listed in the policy don't match your domain's MX records.
- The MTA-STS policy has changed without rotating the ID in the
_mta-stsDNS record. - The MTA-STS policy has been removed without following the proper procedure to flush policies cached by sending mail servers.
Additionally, Cert Spotter provides a dashboard which shows MTA-STS eligibility and deployment status in one place. You can use this dashboard to track MTA-STS deployment across your entire domain portfolio:
Automatic Policy Publication
Deploying an MTA-STS policy initially requires:
- Publishing a text file over HTTPS at
mta-sts.YOURDOMAIN, which requires a valid certificate formta-sts.YOURDOMAIN. - Publishing a DNS TXT record at
_mta-sts.YOURDOMAINcontaining the ID of the policy.
Maintaining an MTA-STS policy on an ongoing basis requires:
- Renewing the HTTPS certificate for
mta-sts.YOURDOMAIN. - Changing the policy any time you change your domain's MX records.
- Changing the TXT record's ID any time you change the policy.
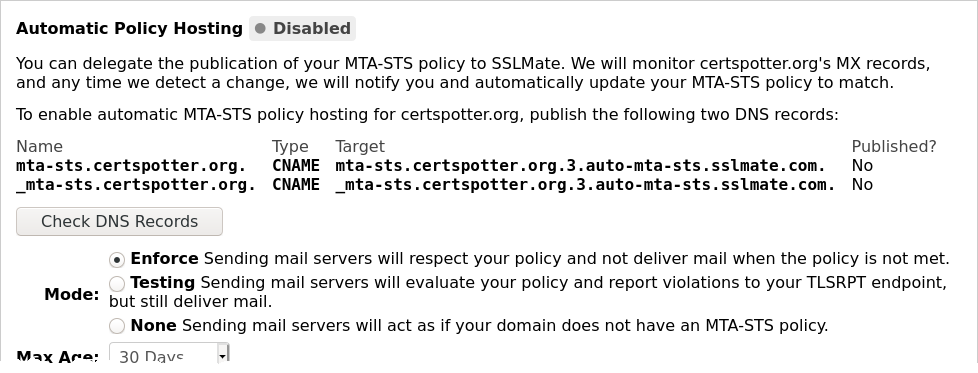
Cert Spotter can optionally automate the above steps. All you need to do is create DNS
CNAME records pointing mta-sts.YOURDOMAIN and _mta-sts.YOURDOMAIN to domain names
hosted by SSLMate. We'll automatically publish a policy matching your MX records.
For transparency, we'll alert you any time your MX records change, so you can take
corrective action if the change was unauthorized. To set up automated MTA-STS,
visit the endpoint page for your domain to retrieve the necessary DNS records and
configure policy settings like the enforcement mode and the maximum age:
Final Thoughts
Email is a critical communication tool, and despite its flaws, it's here to stay. It deserves the same level of encryption and authentication that we take for granted with web browsing. MTA-STS is a major step in that direction, and Cert Spotter is here to help you easily and fearlessly deploy MTA-STS on your domains. Sign up for Cert Spotter today
